Layer 2 Security: How Blockchain Scaling Stays Safe
When you hear Layer 2 security, a set of protocols designed to protect transactions processed off the main blockchain while still relying on its finality. Also known as scaling solutions, it’s what lets networks like Ethereum handle thousands of transactions per second without turning fees into a joke. Without it, blockchains would be too slow and expensive for everyday use. But speed alone isn’t enough—security has to match. That’s where Layer 2 security steps in: it doesn’t just move work off-chain, it makes sure that work can’t be faked, stolen, or reversed.
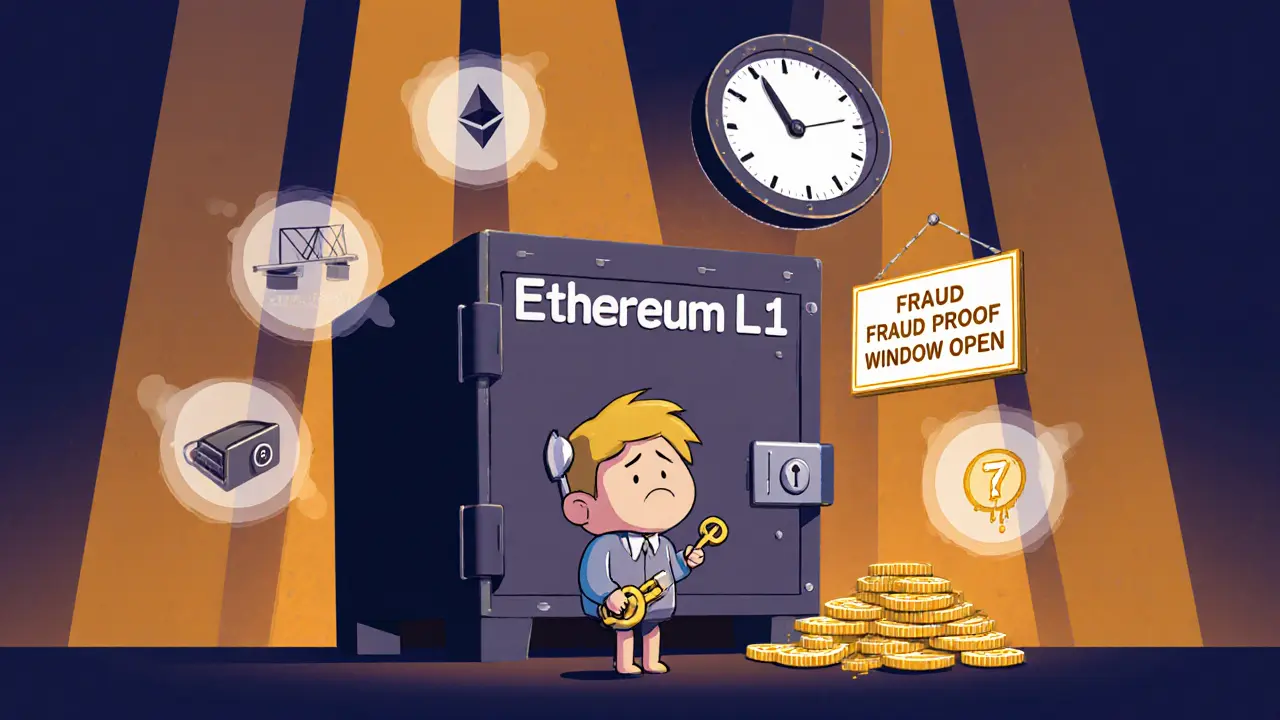
Two main types of Layer 2 systems dominate: zk-rollups, a method that bundles hundreds of transactions into a single cryptographic proof verified on the main chain, and optimistic rollups, a system that assumes transactions are valid unless someone challenges them within a set time window. Both use math, not trust, to keep things safe. zk-rollups rely on zero-knowledge proofs—complex math that proves something is true without revealing the details. Optimistic rollups use fraud proofs, where anyone can spot a bad transaction and trigger a verification on the main chain. Neither needs you to watch every transaction. You just need to know the system can catch lies.
Layer 2 security isn’t just about tech—it’s about incentives. If a validator tries to cheat on an optimistic rollup, they risk losing their entire stake. That’s why real systems require deep pockets to operate. And when you combine this with the security of Ethereum’s main chain—where billions of dollars are locked in—your funds stay protected even if the Layer 2 layer has a glitch. It’s like having a vault (Ethereum) with a secure backdoor (Layer 2) that only opens when the right codes are verified.
What you’ll find below are real-world examples of how Layer 2 security works—or fails. Some posts break down how projects like Arbitrum and zkSync use these methods. Others expose scams pretending to be Layer 2 platforms. You’ll see how 2FA bypass attacks target users of popular rollups, how Merkle trees verify transactions without loading the whole chain, and why some "Layer 2" tokens are just hype with no real security backbone. This isn’t theory. It’s what’s happening right now, with real money at stake.